What is the Cyber kill Chain Concept?
As business owners we either know a lot about cyber security services or we do not. Here we are going to educate you on how threat actors conduct a cyber-attack on a business . This is referred to as the Cyber Kill Chain.
Cyberattacks Are Not a Single Event, They Unfold Through a Series of Certain Steps.
Cyber Kill framework identifies seven key stages of a cyberattack, from initial planning to final impact.
This approach helps security teams understand how adversaries operate, enabling them to stop cyber threats early in the process and prevent damage to an organisation.
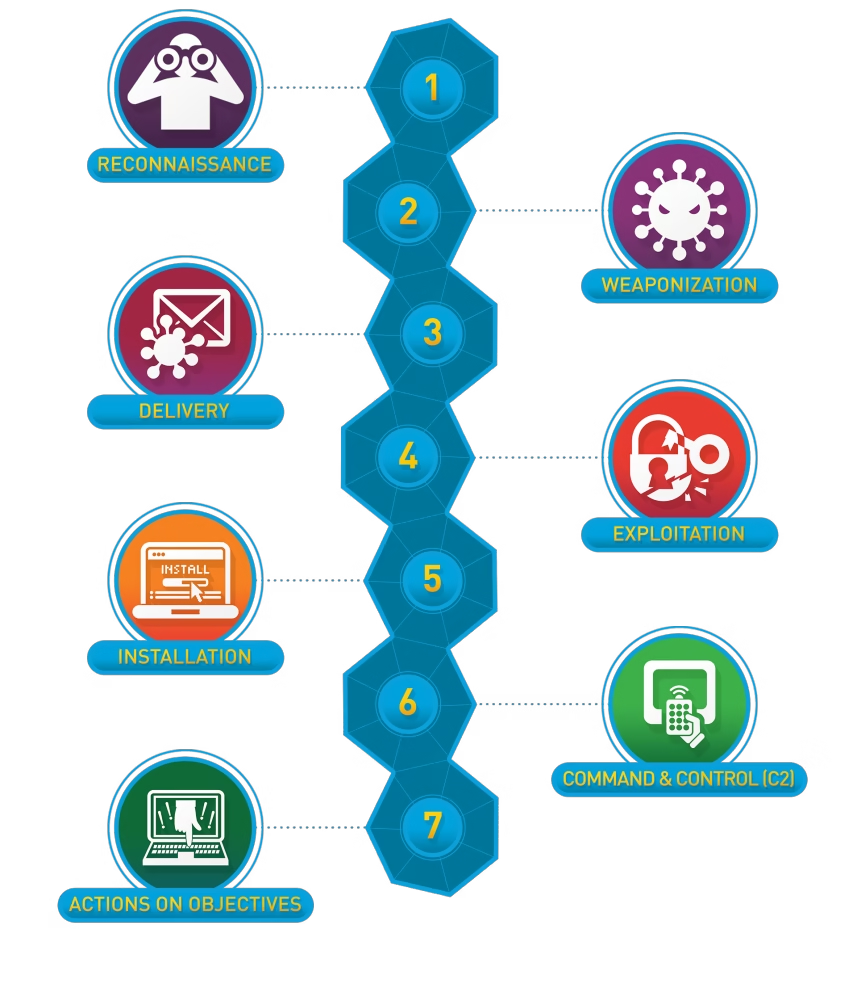
The Seven Key Stages of The Cyber Kill Chain Process
- Reconnaissance: The attacker gathers information about the target.
- Weaponisation: The attacker creates a malicious payload.
- Delivery: The attacker sends the payload to the target.
- Exploitation: The payload is triggered, exploiting a vulnerability.
- Installation: The attacker installs malware on the target system.
- Command and Control: The attacker establishes a command-and-control channel.
- Actions on Objectives: The attacker achieves their goals, such as data theft or system disruption or Ransome.
 Cited : https://www.lockheedmartin.com/
Cited : https://www.lockheedmartin.com/
Understanding these seven stages of the cyber kill chain process is crucial for business owners to recognise the signs of a cyberattack and take initiative-taking measures to protect their organisation.
What Are the Actual Signs of a Cyberattack?
The Attacker’s Research Phase – Reconnaissance
Before launching an attack, cybercriminals gather intelligence about their target, much like a competitor studies a market before entering.
During this reconnaissance phase, attackers seek information that can aid their infiltration.
- Harvesting information on your website, social profiles, and leaked databases to find employee names, job roles and email addresses.
- Scanning for technical vulnerabilities in your business websites and servers.
- Sending out test phishing emails to see which employees respond to the fake emails.
Signs of Reconnaissance
You might notice signs of reconnaissance in your website analytics data, such as specific employee names being searched, unusually high traffic to company websites and social media.
Traffic generated from sources like AI and web scraping tools can also indicate potential reconnaissance.
If your already using cyber security tools, like WatchGuard. You will be able to see these tools generate specific types of traffic that can be detected and monitored by cybersecurity systems.
For example, tools like Acunetix, Nmap, Nessus, OpenVAS, Burp Suite, QualysGuard, and OWASP ZAP will produce network traffic patterns that can be identified by intrusion detection systems (IDS) and security information and event management (SIEM) systems.
Monitoring this traffic can help you identify potential reconnaissance activities and take appropriate actions to secure your systems.
It is imperative for business owners to have cybersecurity tools like WatchGuard and dark web monitoring in place to detect and monitor potential threats, ensuring the protection of their organisation from cyberattacks and data breaches.
How They Craft Attack Tools – Weaponisation
After gathering sufficient information, attackers create their tools, such as malicious files, harmful scripts, or software exploits, to infiltrate the target’s systems.
They customise these tools based on their findings, like preparing specific exploits for outdated software or crafting fake emails with malicious attachments.
Many attackers use ready-made exploit kits from the dark web, needing only the right tool for the job.
Weaponisation tactics involve creating tools to infiltrate a target’s systems. Examples include:
- Malicious files: Attackers create harmful files designed to exploit vulnerabilities.
- Harmful scripts: Scripts that can execute malicious actions on the target’s system.
- Software exploits: Customised exploits targeting specific vulnerabilities in outdated software.
- Fake emails: Crafting emails with malicious attachments to deceive employees.
- Exploit kits: Ready-made kits from the dark web used to conduct attacks.
- Ransomware: Malware that encrypts files and demands payment for decryption.
- Trojan Horse: Malicious software disguised as legitimate to gain access.
- Worm: Self-replicating malware that spreads across networks.
- Virus: Malicious code that attaches to programs and spreads between systems.
- Rootkit: Tools that hide malware and maintain unauthorised access
- Fake Webpages: Fake webpages are deceptive sites that mimic legitimate ones to exploit users’ trust in brands.
What You Need to Watch for at This Point
At this stage, the attacker is just waiting for someone to take the bait—a single click or misconfiguration can open the door to the next phase.
Delivery of the Payload
In this phase, the attacker delivers the malicious payload. This can happen through:
- Compromised websites: Visiting an infected site can download malware in the background.
- Phishing emails: Fake emails trick people into opening harmful attachments or clicking bad links.
- Software vulnerabilities: Attackers exploit security flaws to inject malicious code.
Once they have access to systems the next step is, Exploitation.
Exploitation – The Payload Is Triggered, Exploiting A Vulnerability
In the exploitation phase, the attacker activates the malicious payload, taking advantage of a vulnerability in the target system.
This could be a flaw in software, an unpatched security hole, or a misconfiguration.
For UK businesses without robust cybersecurity measures, it is crucial to regularly update software and apply security patches to minimize these vulnerabilities.
Ignoring these updates can leave systems exposed to exploitation, leading to severe consequences.
Installation – The Attacker Installs Malware on The Target System
Once the vulnerability is exploited, the attacker proceeds to install malware on the target system.
This malware can range from spyware to ransomware, each designed to disrupt operations or steal sensitive data.
UK businesses should be vigilant for signs of malware, such as unusual system behaviour, slow performance, or unexpected pop-ups.
Implementing basic cybersecurity practices, like using antivirus software and conducting regular scans, can help detect and prevent malware installation.
The Attacker Establishes a Command-and-Control Channel
In this phase, the attacker sets up a command and control (C2) channel to communicate with the compromised system.
This channel allows the attacker to issue commands and control the infected system remotely.
UK businesses should monitor network traffic for unusual patterns or connections to unfamiliar servers.
Employing network security tools and intrusion detection systems can help identify and block these C2 channels before they cause severe damage.
Watchguard Tools Can Monitor for This Behaviour Here is How…
Intrusion Prevention Service (IPS)
WatchGuard’s Intrusion Prevention Service uses continually updated signatures to scan traffic across all major protocols. It provides real-time protection against network threats, including spyware, SQL injections, cross-site scripting, and buffer overflows.
By identifying and blocking suspicious activities, IPS can prevent attackers from establishing C2 channels.
ThreatSync+ NDR
ThreatSync+ Network Detection and Response (NDR) is a cloud-based solution that leverages advanced AI to analyse network traffic, identify suspicious activities, and issue real-time alerts.
This initiative-taking approach helps businesses quickly investigate and respond to potential attacks, preventing them from causing severe damage.
Basic Security Suite
WatchGuard’s Basic Security Suite includes a range of network security services such as IPS, Gateway Antivirus, URL filtering, application control, spam blocking, and reputation lookup.
These tools work together to provide comprehensive protection, making it difficult for attackers to establish C2 channels.
For UK businesses without cybersecurity protection, implementing WatchGuard’s solutions can significantly enhance their ability to detect and block malicious activities, safeguarding their operations and data.
Actions On Objectives: The Attacker Achieves Their Goals, Such as Data Theft or System Disruption or Ransom
Finally, the attacker reaches their objectives, which may include stealing sensitive data, disrupting business operations, or demanding ransom.
For UK businesses, the impact of such attacks can be devastating, leading to financial losses, reputational damage, and operational downtime.
It is essential to have a response plan in place, including regular data backups, employee training on cybersecurity best practices, and a clear protocol for handling incidents.
Being prepared can mitigate the effects of an attack and ensure a quicker recovery.
Takeaway Summary: Spotting Cyberattack Damage Before It Happens
What to Watch For:
- Reconnaissance: Look for unusual website analytics data, such as specific employee names being searched or unusually high traffic. Cybersecurity tools can help detect traffic from reconnaissance tools.
- Weaponisation: Be aware of malicious files, harmful scripts, and fake emails. Regularly update software and train employees to recognize phishing attempts.
- Delivery: Watch for phishing emails, compromised websites, and software vulnerabilities. Implement email filtering and web security solutions.
- Exploitation: Ensure software is up-to-date and security patches are applied. Monitor for signs of exploitation, such as system slowdowns or unexpected behaviour.
- Installation: Look for signs of malware, such as unusual system behaviour or pop-ups. Use antivirus software and conduct regular scans.
- Command and Control: Monitor network traffic for unusual patterns or connections to unfamiliar servers. Employ network security tools and intrusion detection systems.
- Actions on Objectives: Have a response plan in place, including regular data backups, employee training, and clear incident handling protocols. Being prepared can mitigate the impact of an attack and ensure a quicker recovery.
By understanding and monitoring these stages, business owners can spot potential cyber threats early and take action to prevent damage to their organisations.
Implementing robust cybersecurity measures, such as those offered by WatchGuard, and using a managed IT support provider like Speedster IT, can significantly enhance your ability to detect and block malicious activities, safeguarding your operations and data.

With over 15 years at Speedster IT, I’ve built a career around helping businesses navigate the evolving world of technology. I publish all the content for the IT Support London Blog and Cyber Security Blog, where I share practical insights on infrastructure upgrades, cybersecurity trends, and smart IT strategies for growing companies.
